Trump’s 2025 Cybersecurity Executive Order: What Contractors Need to Know

Introduction
On June 6, 2025, the Trump Administration unveiled a new cybersecurity Executive Order (EO), titled “Sustaining Select Efforts to Strengthen the Nation’s Cybersecurity”, which amends and updates the Obama-era EO 13694 and Biden-era EO 14144.
Key Changes in the 2025 Executive Order
1. Policy Realignment and National Threats
The EO replaces Section 1 of EO 14144 with a renewed policy focus:
-
Strengthening digital infrastructure
-
Protecting vital cyber services
-
Enhancing capabilities to counter foreign cyber threats
It reaffirms China as the top cyber threat, followed by Russia, Iran, and North Korea.
Strategic Edits to Previous EOs
2. EO 14144 Amendments
While large sections of EO 14144 are revised or removed, some areas—like the cybersecurity of federal systems and national security systems—remain intact.
-
The entire section on “Solutions to Combat Cybercrime and Fraud” is deleted, eliminating federal grant programs for digital identity verification and mobile IDs.
3. EO 13694: Targeted Sanctions Refined
The language is changed from targeting “any person” to “any foreign person” in terms of cyber sanctions. This reduces the risk of sanction misuse against domestic political groups and clarifies that election-related activities are exempt.
Software Supply Chain Security: A Major Pivot
The EO walks back several Biden-era mandates directing software providers to submit secure software attestations and artifacts to CISA. Instead, responsibility shifts toward NIST, reducing CISA’s operational role
NIST Directives Under the EO:
-
By August 1, 2025: Create a public-private consortium at the National Cybersecurity Center of Excellence to provide new guidance based on NIST SP 800-218 (SSDF).
-
By September 2, 2025: Update NIST SP 800-53 to address secure deployment of patches and updates.
-
By March 31, 2026: Finalize a revised SSDF with added examples and development procedures.
FAR Updates: Deadlines and Targets
The EO sustains previous plans to revise the FAR, although none of the initiatives have officially been added to the Open FAR Case list (a necessary step before rules become enforceable). Still, the EO sets these tentative timelines:
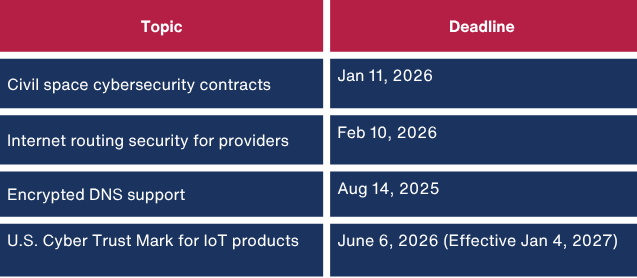
While these deadlines offer a roadmap, implementation delays are likely due to regulatory processes.
What This Means for Contractors
Contractors providing software, digital products, or cybersecurity solutions to federal agencies should closely monitor:
-
Shifting authority from CISA to NIS
-
Changes to attestation requirements under FAR Case 2023-002 .
-
Upcoming FAR clauses involving IoT, encrypted DNS, and internet routing technologies
-
Industry consortium developments at NIST
